DDoS X Protect hardware appliances
DDoS X Protect hardware appliances
«Protection against Distributed Denial-of-Services (DDoS) shouldn't come at the cost of a brand-new luxury car for your business. Almost any digital business on the planet is exposed to the risk of being attacked today or tomorrow at noon. We have elaborated on everything possible with the current IT technology stack to stop and block DDoS attacks on your infrastructure. And it all comes to you with the price tag of a moderate laptop.» ‒ our team vision throughout the years of research and development.


DDoS. What is it in the first place?
The National Institute of Standards and Technology describes Distributed Denial-of-Service as a technique that uses numerous hosts to perform an attack on a victim organization. Have you never experienced the unpleasantness of a DDoS attack? Consider yourself fortunate! In our attempts to persuade you to buy our solution, we could attach a nice-looking PDF of statistics that report the global frequency of such incidents and try to scare you. But we won't do so. You can find those articles on your own. If you are already seeking a solution to this global challenge, we are here to share our experience in the form of DDoS X Protect hardware appliances.
Why hasn't fail-proof DDoS protection been invented yet? Our answer is because of the very nature of the Ethernet protocol itself and the IP packet delivery technique across the Internet. Imagine that the entire planet is sharing a common corridor in a dormitory. Yes, that's our Internet. Everyone can come and start knocking on your door. You got the idea, right? And what if you have a huge and wide channel leading to your door? Start speaking in technical terms: your organization has a dedicated 100 Gb/s provider link connecting you with the others. To saturate such an extremely spacious communication channel, bad guys, in the worst-case scenario, have to generate 148.81+ Mpps (million packets per second) of TCP SYN packets towards your infrastructure to put your system down. That's one of the clearest examples to illustrate the idea. How do you sustain such an abnormal traffic flood and don't lose the ability to serve legitimate user requests? That is what our solution is about.
So, how? In the example mentioned, we only have 463 CPU cycles available on a particular CPU core where the incoming packet was fetched. This means that the algorithm inspecting every Ethernet frame should not exceed this threshold to sustain Denial-of-Service attempts and prevent link saturation. Is it a big or small number? The light beam is traversing around 15 cm per single CPU cycle at 2 GHz speed, and to stay unblocked, we have a timeframe available for every single packet inspection while the light passes around 70 meters. Is it possible at all? We would say 'No'... until recent times. Till then, it was only possible for multi-billion-dollar IT giants to design their own FPGAs, ASICs, and purpose-built on-die chips dedicated to performing those kinds of operations. So, what about 'Now'?
Yep... and the answer is the DPDK project our solution is based on.
Reaction Time.
If you are a regional cloud provider, a well-known broadcast media agency, a local shop, or any other digital business servicing user requests on the Internet, you will barely be reading this long text while a DDoS attack is underway. It's a bit late for you. Currently, your technical team is fully overloaded with exploring tools and methods to absorb the dozens of Mpps hitting your backbone routers and other infrastructure elements. It is worth mentioning that human reaction is negligibly slow compared to the speed of network devices, which can generate millions of diverse malicious packets per second. Yes, we strongly believe your IT staff are outstanding experts in all relevant domains of knowledge and are able to handle every possible attack vector in the blink of an eye. But reality is usually more down to earth. If you are under attack, almost for sure, only the opposite side can relieve the pressure on you. During the prepaid attack time, they are controlling what is happening with your business, not you.
Unless you're on the list of TOP5 public cloud providers, of course.

DDoS X Protect Appliance Exterior.
All X Protect models come in rugged housing and with exactly two Ethernet ports: one dedicated for the incoming link from your ISP (or upstream link if you are an ISP yourself), and the second connecting to your Local Area Network. Depending on the model, network speeds are 1/2.5 Gb/s (copper or optics), 10/25 Gb/s optics, and the mind-blowing 100 Gb/s.

Download Full Specs.
Download DDoS X Protect technical specifications.
Wish to get accustomed to terminology used in attacker's world? We recommend you read a publication at ResearchGate. Or deep dive into DPDK framework right away at DPDK.org
All Complexity Remain Inside.
Humans are not players on this field, a fact you knew well before reading it here. The only chance to prevent a successful and long-lasting attack on your organization is to be prepared in advance.
The refinement and strengths of CPU vector operations utilized, the elimination of TLB overheads, the NUMA affinity, and the complexity of modern processors' cache coherence mechanisms while dealing with timeframes measured in nanoseconds – all of that remains inside the X Protect box you connected to your network infrastructure.
From your point of view, you have a watchdog scrutinizing every network packet passing by and reacting immediately when deviations are detected. "Immediately" means within a magnitude of microseconds.
The major challenge all DDoS protection devices and methods face is not simply blocking abnormal packet flow, but being smart enough to pick out legitimate traffic and continue serving real customer requests while under attack. This is a piece of low-level assembler code that we constantly improve in our algorithm, month-by-month. However, nothing is perfect, so all X Protect appliances are equipped with a physical key that allows you to switch the device back to LISTEN mode, bypassing network traffic inspection and filtration. Bad story... we agree, but that gives you an option to run 'as-is' while we, together with the rest of the world, figure out new methods attackers invent to break through.

Security Aspects.
The solution works purely at the Ethernet frame level, or as described in the OSI model, at layer II. It is fully transparent and not accessible directly or indirectly, locally or remotely. Because of this, the box itself cannot become an attack vector. Furthermore, neither you as an owner nor we as developers can do anything without physically touching it. To be clear: there is no TCP/IP stack, no IP addresses, and zero chance to access the appliance remotely, switch it off, or disrupt its functionality beyond physically removing cables. Therefore, don't expect any visually appealing reports or graphs, the ability to tune parameters, or configure it; all this is not possible with DDoS X Protect appliances. Local console? Not available either.
Want to be sure the X Protect device itself is not a spy tool? Honestly, we wouldn't be delighted to sell our solution to your company if you don't ask that question. External traffic analyzers can give you the desired answer, not us.

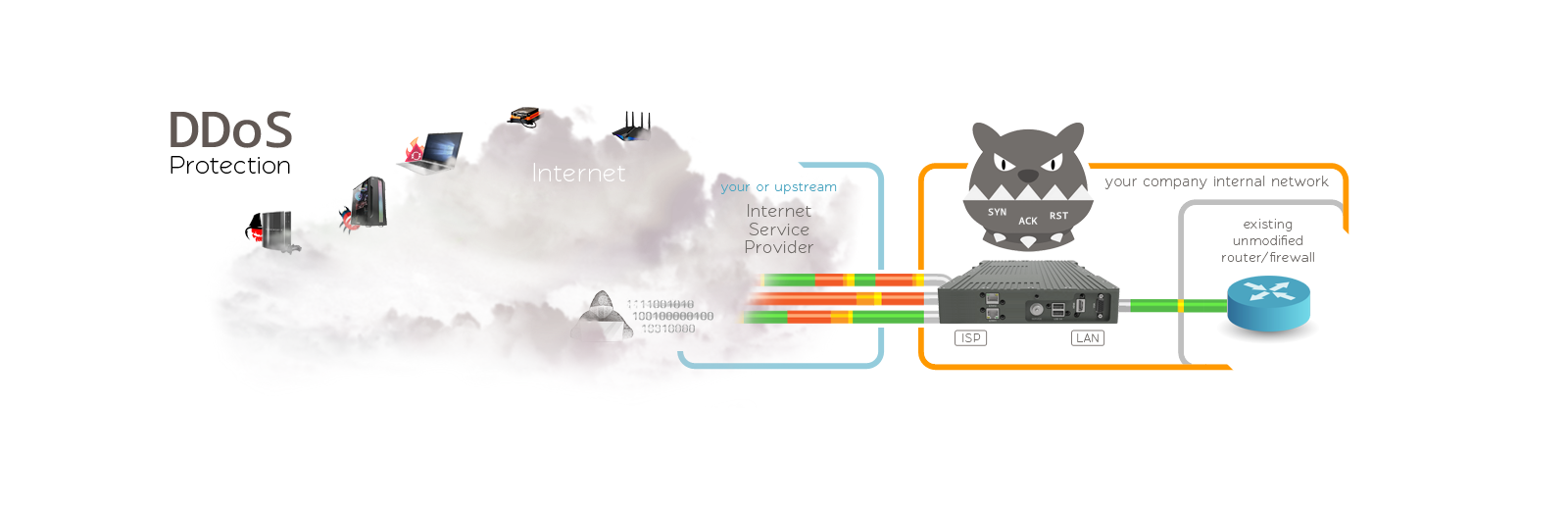
Network Diagram.
As shown in the diagram, the DDoS X Protect appliance sits in the front of your existing router or firewall. Transparency at the network level provides numerous benefits described earlier, but one of the most noticeable is the simplicity of device integration into the existing infrastructure. This step requires zero configuration. Nothing needs to change on either side. Everything, including IP addresses, CIDR ranges, and VLAN tagging, remains original while the DDoS X Protect box is attached and running. Sounds like magic!? Yes, kind of. It's by design.
DDoS X Protect models and Support.
Our main distribution channel is Amazon.com. That is safe and trustworthy, both for you as a buyer and for us as a seller. Additionally, we accept direct-sale orders starting from 5 devices. If your organization's policies do not allow purchases from Amazon.com, please contact our sales department, and we will find the most appropriate delivery and payment method for you. High-end DDoS X Protect models intended to work at 40 and 100 Gb/s link speeds are exclusively sold via invoicing and initial purchase agreement. These high-end models are currently built on the Dell XR5610 ruggedized 1U server with Intel® Xeon® Gold 6438N processor.
The actual model selection is always found at the very beginning of this webpage. Your appliance comes with a perpetual lifetime license, allowing you to use it without time restrictions. Each device has a sticker with a unique 16-symbol identification number. For the first twelve months from the delivery date, you receive a standard hardware warranty plus access to software updates. A subscription can be further extended for one, two, or three years. During this period, you are covered by the hardware warranty and have the right to download and update the software on your X Protect device, as well as request technical support through our ticketing system. Please note that the software is tightly coupled with the unique identifier found on the sticker, and the system will not allow updates if they do not match.
+1 year of support
$200 (est. €185) VAT excl.
- 1 year of hardware support extention
- 1 year of access to software updates
- 1 year of access to our support
+2 years of support
$280 (est. €260) VAT excl.
- 2 years of hardware support extention
- 2 years of access to software updates
- 2 years of access to our support
+3 years of support
$350 (est. €325) VAT excl.
- 3 years of hardware support extention
- 3 years of access to software updates
- 3 years of access to our support
DDoS X Protect Appliance Setup.
The DDoS X Protect device arrives at your site ready to use. There is no need to reconfigure IPv4/IPv6 addressing scheme, VLAN tagging, security policies, or any other aspect of your datacenter's Internet connection. The device itself tears apart the communication link between an upstream provider's router/switch port (or incoming optical cable) and your organization's first facing network device, usually a router or firewall. Insert the incoming cable into the port labeled ISP on the front of the appliance. Use the second cable (not included due to varying lengths, thicknesses and other parameters) to connect the port labeled LAN to the original inbound port on your switch or router. If you ordered a model with long-range single-mode optical Ethernet connectors, the second pre-installed SFP/SFP+/SFP28 module is a low-transmit power variant (up to 300m). To avoid excess signal power in the fiber cable now connecting your router/firewall to the DDoS X Protect LAN port at a shorter distance, it is highly recommended to replace the original optical module with a low-transmit power variant or use a passive optical signal attenuator for its Transmitter [TX] fiber core. For copper RJ-45, multi-mode, or SR (short-range) single-mode optical links, no additional adjustments are needed.
What People Are Saying.
Get Notifications About Newer Versions.
Adding your own MailChimp powered email sign-up is easy. Grab the super slim code from your MailChimp account and drop the code here. Lastly, remove the link and style tags that comes with the embedded code and your good to go. All styling is within our stylesheet.
We never share your information or use it to spam you.
Our future work...
We work hard to make everything real. The expected product General Availability is Q4'2024. Please notify us of your interests and desires now, it will help us better prioritize our tasks! Share your thoughts with us using the Early-Bird form seen on the left side. We are ready to give you up to 25% discount on the final unit price if your idea or requirement is unique and helps our team make DDoS X Protect solution even better.
In development
Future per month
- In development
- In development
- In development
- In development
- In development
- In development
In development
Future per month
- In development
- In development
- In development
- In development
- In development
- In development
In development
Future per month
- In development
- In development
- In development
- In development
- In development
- In development
In development
Future per month
- In development
- In development
- In development
- In development
- In development
- In development